Today, we dive into Identity Auditing & Monitoring — one of the most overlooked yet critical layers of identity management. Whether you manage an on-prem Windows Server, a hybrid Azure AD setup, or a Linux Server, monitoring user behavior and identity-related events is key to detecting insider threats, policy violations and misconfigurations in real time.
🧠 Why Identity Auditing & Monitoring Matters
- 🛡️ Security: Track logins, privilege escalations and abnormal behavior.
- 📜 Compliance: Required for standards like ISO 27001, HIPAA, PCI-DSS, etc.
- ⏱️ Forensics: Enable investigation of who accessed what and when.
- 🔔 Alerting: Prevent incidents before they escalate.
🔍 1. Windows Server (Active Directory)
🔑 What to Monitor:
- Logon/logoff events (Event ID 4624/4634)
- Account lockouts (4740)
- Privilege use (4672)
- Group membership changes (4728/4729)
- New user creations (4720)
🔧 Tools:
- Event Viewer: Local and remote audit log inspection.
- Group Policy: Enable Advanced Audit Policy Configuration.
- Sysmon + Windows Event Forwarding (WEF): Collect logs centrally.
- SIEM Tools: Send logs to Splunk, Microsoft Sentinel, or Graylog.
powershell
AuditPol /get /category:Logon/Logoff
📌 Pro Tip:
Use PowerShell with Task Scheduler to email alerts for specific Event IDs.
☁️ 2. Azure Active Directory (Entra ID)
Azure AD includes cloud-native auditing and monitoring features out-of-the-box.
🔍 Key Identity Logs:
- Sign-in logs: Who logged in, from where, using what method.
- Audit logs: Password resets, group changes, license assignments.
- Conditional Access Insights: Policy results and failures.
🔧 Tools:
- Microsoft Entra Admin Center → Monitoring → Audit Logs & Sign-ins
- Microsoft Sentinel: Advanced log correlation and threat detection.
- Graph API / KQL Queries: Automate extraction of specific identity events.
kusto
SigninLogs
| where ResultType != 0
| project UserPrincipalName, IPAddress, Status
🔐 Pro Tip:
Enable Identity Protection to detect risky sign-ins and compromised accounts based on behavior analytics.
🐧 3. Linux Server (LDAP/SSSD Integrated)
🔍 What to Monitor:
- Login attempts via /var/log/auth.log or /var/log/secure
- sudo command executions
- User add/modify/delete events
PAM (Pluggable Authentication Module) failures
🔧 Tools:
- auditd: Linux Audit Daemon for tracking system calls.
- Logwatch / Logrotate: Email summaries of suspicious activities.
- fail2ban: Detect and block brute-force login attempts.
- Auditbeat + Elastic Stack: For visual dashboards and alerting.
bash
ausearch -m USER_LOGIN,USER_START -ts today
📌 Pro Tip:
Use auditctl rules to track changes to /etc/passwd, /etc/shadow and group files for identity tampering.
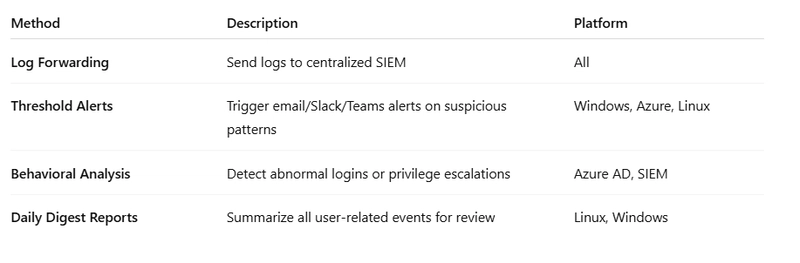
📊 Real-Time Monitoring Strategies
🛠️ Tools That Make Monitoring Easy
🧩 Wrapping Up
Effective identity monitoring and auditing isn't optional anymore. Whether you're operating in a hybrid or pure-cloud environment, having visibility and control over identity-related events is essential for:
✅ Proactive security
✅ Policy enforcement
✅ Compliance readiness
✅ Quick incident response
Even if you're a solo developer or a small IT team — start with baseline auditing and automate alerts over time. Trust me — future-you (and your security team) will thank you.