This is a submission for the Pulumi Deploy and Document Challenge: Shhh, It's a Secret!
Securely sync community feedback from Telegram to Slack and back — all managed with Pulumi ESC.
What I Built
Meet Catherine 👩💻👋.
She’s a Senior Project Manager at a growing tech startup. To collaborate better, Catherine created a Telegram group with her interns.
But there’s one big problem that makes Catherine anxious...
From time to time, one of the interns accidentally posts a secret in the group.
For example:
"Hey, I tried this one: ghp_FAKEtoken123456789, but it didn’t work 😭"
For Catherine, this is a serious risk:
- Tokens could be misused
- Systems could be compromised
- The startup’s data could be leaked The worst part? Catherine doesn’t have time to monitor the group 24/7. Catherine decides to use antileaked.io, a smart Telegram bot that can:
- Watch all messages in the group
- Detect any leaked tokens or passwords
- Check if the leaked secret matches something stored in 1Password
- If it does, rotate (change) the secret automatically
- Send a notification to a special channel for Catherine (as the team lead)
Now Catherine doesn’t need to stress or act like a group moderator.
antileaked.io runs quietly in the background, protecting her team without interrupting their workflow.
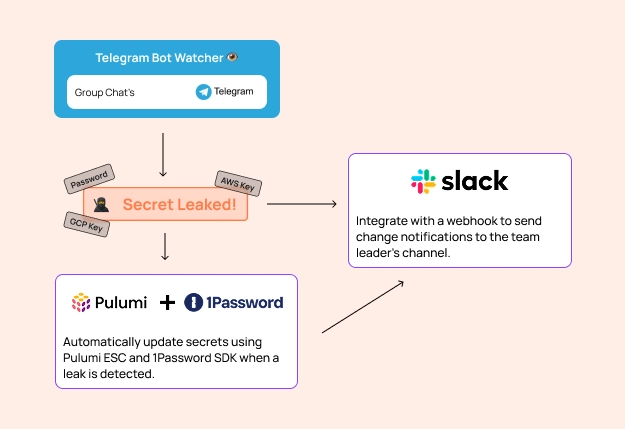
How does this work?
Just simple like that! but powerfull tools!
Live Demo Link
You can try joining the group I've created.
The group is monitored by a bot I’ve built (@Bridge4Buildbot).
Once you're in, you can try sending a message that contains a secret key — I’ve prepared some examples below.
values:
dev:
apiKey: VBCeZwSAzAFJPoxkv4diPvEH
aws_secret_key: AKIAIOSFODNN7EXAMPLE
catherine_gmail_password: op://myStartup Secret Vault/mail/password
gcp_token: ya29.a0ARrdaM-fakeGCPtoken934xz_gT8KJ
gh_token: ghp_9e2jTfA1YkE5JXZUqvNa3dMZo4KvBLpZQ7oN
for see the difference and updated env, please send /env to private chat to @Bridge4Buildbot, It will provide an update on the environment variables that have been changed.
Project Repo
https://github.com/diosamuel/antileaked.io
My Journey
First Setup
The first step is to gather all our secret keys into a 1Password vault.
We can use either the 1Password desktop app or the CLI — in this case, I'm using the desktop app for convenience.
Then, copy the secret reference for each secret that have been created.
An example of a secret reference looks like this:
"op://myStartup Secret Vault/mail/password"
then, insert Secret Reference to .env
catherine_gmail_password=op://myStartup Secret Vault/mail/password
Next step, we must create an ESC Environment at https://app.pulumi.com/
This step is necessary to store secret keys in Pulumi ESC, as well as to integrate with 1Password and Telegram using the Pulumi SDK.
Set Pulumi Slack Webhook 🪝
Let's create a notification to Slack to monitor changes — we can leverage the Pulumi webhook to achieve this on this website.
We can use the Slack App Template provided by Pulumi.
Once we’ve obtained the webhook URL, we can insert it here:

https://app.pulumi.com//webhooks/new
✅ All set! Now, every change will trigger a notification to Slack — in our case, directly to the team leader.
Using Pulumi ESC on-the-go
After creating a Pulumi ESC environment, the next step is to initialize the ESC environment in our project using the ESC CLI and add each environment variable into the ESC environment.
Login to Pulumi ESC:
esc login
Initialize the environment:
esc env init <account>/antileaked/secret
Set 1Password
$Env:OP_CONNECT_HOST=
pulumi config set pulumi-onepassword:url --secret
Store Catherine's password (example):
esc env set <account>/antileaked/secret catherine_gmail_password op://myStartup Secret Vault/mail/password --plaintext
Telegram Bot Watcher + 1Password + Pulumi
The Telegram bot is organized according to this structure.
├── 1password
│ └── index.js
├── node_modules/
├── pulumi
│ └── index.js
├── .env
├── index.js
├── package-lock.json
├── package.json
Here explained file:
index.js
Serves as the main entry point for the Telegram bot. It leverages the powerful Telegraf.js library to handle incoming messages, monitor chat activity for potential secret leaks, and respond to specific commands. The bot is designed to integrate seamlessly with secret management and notification systems to enhance security within group chats.
1password/index.js
This module is dedicated to securely retrieving secrets from 1Password vaults using the official 1Password SDK. It provides a clean interface to access sensitive credentials based on reference paths, making it easy to integrate with other parts of the application that rely on secure, dynamic configuration.
pulumi/index.js:
This file encapsulates all logic related to interacting with Pulumi ESC (Environment and Secrets Configuration) through the @pulumi/esc-sdk. It supports reading, updating, and managing environment secrets programmatically, enabling automated secret rotation and real-time configuration updates as part of the bot’s leak prevention workflow.
This has been an exciting and valuable experience—implementing Pulumi ESC and 1Password together opened up a new level of automation and security for managing secrets. I’ve learned a lot throughout this process, and I’m looking forward to exploring even more integrations in the future!🙌🙌






This is cool!