Recently I had a shower thought about passwords, namely that any rules we apply limit the possible passwords the user can choose. Which also means that there are less passwords an attacker has to go through when brute-forcing a password.
Setup
For simplicity I chose 4 character groups:
- lowercase letters: 26
- uppercase letters: 26
- numerals: 10
- special characters: 34
The calculations assume that there has to be at least 1 character of each group in the password.
This is not exhaustive of course, but I have to start somewhere.
Impact
In total there are 96 allowed characters.
This means, for an 6 character long password, without any rules, there are 96^6, or 782.757.789.696, options. Almost 800 billion.
With the rules above applied, there are only 26*26*10*34*96^2, or 2.118.205.440, options. Just a bit more than 2 billion.
That's a 370x difference!
To put that in perspective, instead of 1 year, it will take an attacker less than 1 day to brute-force that password.
Is that bad?
To be honest, I don't know. It sounds like much, but on the other hand, increasing the length by ~1.3 characters will negate the difference. So a password that's 1 character longer will almost do so, and one that's 2 characters longer will provide even better security.
What are your opinions on that topic? Please comment below 👇
Follow me on Twitter for more of my thoughts, articles, projects and work.












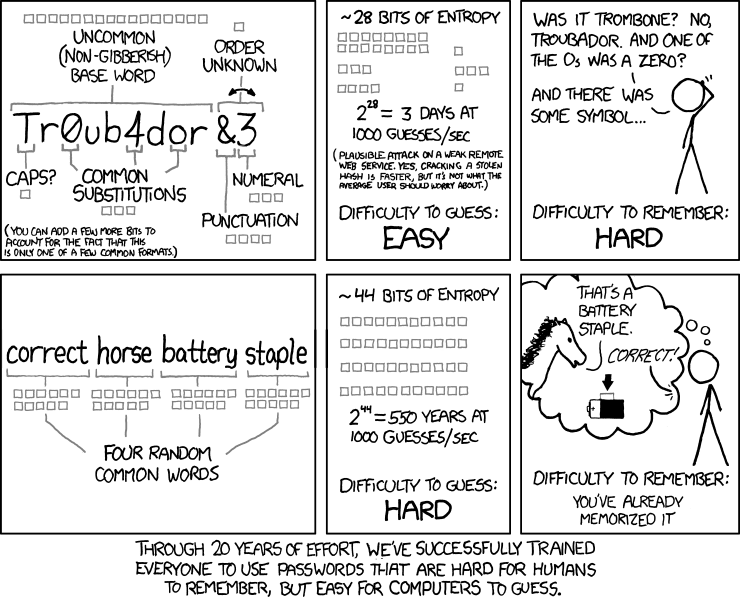



I believe that since the problem is solved by adding a couple more characters to the password it is not really an issue. We are not talking about getting the length up to 20-25 characters but just to 9-10. Which is still quite easy to remember.
Sure, it takes away all the combinations that use characters from some instead of all the character groups you mentioned but it is easily negated by the password length.
Plus the number one rule to make your password "immune" to brute force is making it longer than 8 characters (by today's standards, correct me if I'm wrong). Most of the sites that test passowrd strength suggest so.