SHUBHENDU SHUBHAM articles - 24 total
5 Tips I Wish I Knew Earlier as a Security Architect
Look, I'm not going to sugarcoat it. My last year as a security architect was rough. Really rough. I...
Fixing Bluetooth Issues in Kali Linux
I recently ran into a frustrating problem on my Lenovo Ideapad 5 Pro running Kali Linux — Blueman...
The Docker Diet: How I Lost 1.1GB in 5 Steps
Last week, I was staring at a 1.2GB Docker image wondering where I went wrong. The build took...
No More Secrets in State! Write-Only Arguments in Terraform 1.11
If you’ve been working with Terraform for a while, you’ve probably run into this frustrating...
My Firebase Webapp almost got pwned by a bot. Then another bot saved it.
My Firebase Webapp almost got pwned by a bot. Then another bot saved it. Running Firebase 9.22.1 in...
Resolving Docker Socket and Daemon Conflicts: Unifying CLI and Docker Desktop on kali Linux
If you're using Docker Desktop on Linux and facing issues like conflicting results between docker ps...
Missing Dark Mode in Wazuh ?
Working on Wazuh in a bright interface can sometimes strain your eyes, especially during those long...
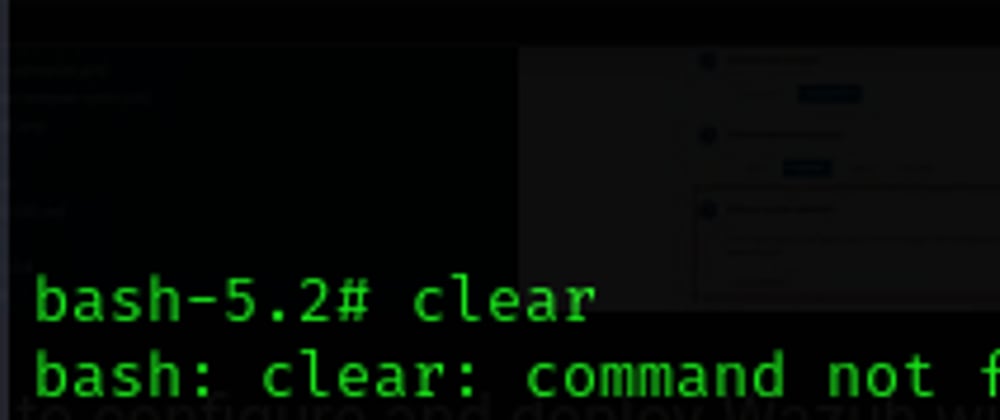
Clear command not found inside docker container ?
if you're inside docker container using cli trying to modify files and wanna clear yout terminal ,...
Upgrading wazuh 4.11.0 using docker in single node
In Feb Wazuh released V4.11.0 let's understand what are the major updates and how to upgrade it using...
Fix It Before They Break It: The True Role of Vulnerability Management
Before we start let's understand a few keywords Vulnerability: Vulnerability is always defined by...
How to troubleshoot a Disconnected Wazuh Agent in a Docker Single-Node Environment?
In this blog post, we'll walk through the steps to troubleshoot and resolve a disconnected Wazuh...
Mitigating vs Eliminating Threats
In security industry I have often seen people getting confused or thinking both as same Mitigating...
Understanding OWASP Top 10 for LLMs: A Layman’s Guide
In the world of AI, Large Language Models (LLMs) like GPT-4 and (o) are becoming increasingly...
Why SysLogs over UDP is silly? Security POV
Before we start let's understand Logs in terms of Threat Modeling STRIDE framework. Here addressing...
"KQL Showdown: distinct vs project"
I'm writing this short blog while solving challenge at KC7 platform, this question hit me when to use...
Why “Think Like an Attacker” is harmful FT: Threat Modeling?
Before we start , just quick reminder it’s Threat Modeling not Modelling. Now let recall basic...
Why Current Methods Fail to Measure Real Vulnerability Risks?
In today's dynamic digital landscape, safeguarding data and infrastructure requires not just...
How to integrate Docker Scout with Azure Container Registry
Before starting, let’s understand what exactly is Docker Scout? Docker Scout is a container image...
Effortless Wazuh v4.10.0 upgrade using Docker
Upgrading your wazuh docker deployment to the latest version ensures you benift from the latest...
5 G : Era of Smart World
Large-scale convergence(LSC),is not about the convergence of different technologies. It is about deve...
How to set Proxy for Docker Containers in Linux Machines?
In the era of automation everyone is deploying on Docker(52%) & Kubernetes (30%) globally. sound...
How to install Docker in Parrot os ?
Following steps:- INSTALL DOCKER ENGINE add user to docker group for using docker command without...
HOW TO USE GIT FOR WORDPRESS DEVELOPMENT???
Let's first understand GIT:- GIT : A BRIEF INTRODUCTION Git is a version control system.This versi...
Top 10 Hottest Kubernetes tools and Technologies of 2019
Rancher K3 Red Hat codeReady WorkSpaces Styra DAS TrilioVault for kubernetes Pivotal Build Service K...