Articles by Tag #owasp
Browse our collection of articles on various topics related to IT technologies. Dive in and explore something new!
Segurança no Front-end: dos ataques à prevenção
Se você ainda acha que segurança na web é responsabilidade exclusiva do back-end ou do time de...
Segurança no Desenvolvimento: Da Teoria à Prática – Introdução
Pensando em segurança no desenvolvimento de software, onde geralmente a incluímos? Como pessoa...
OWASP Top 10 Is Just the Start: How WAFs Defend Against Real Attacks
If you've ever read the OWASP Top 10, you already know the most common web vulnerabilities—like SQL...
SafeLine WAF Automation: Real-World Security Ops Example (Case 1)
Background In modern web environments, real-time visibility and automated responses are...
OWASP Global AppSec SF 2024: Empowering Developer Security As A Community
Only one section of the Mississippi River runs East to West. That stretch of the Big Muddy is home to...
Broken Access Control in React: Fixes & Code Examples
Broken access control happens when users can reach pages, APIs, or data they’re not allowed to. In...
🛡️ OWASP Top 10 (2021 Edition) — Explained
# Name Description Example A01 Broken Access Control Users can access resources or perform...
5 Common Security Mistakes Developers Still Make (and How to Fix Them)
Hey there, fellow developers! 👋 We all know security isn't just a "DevOps thing" or a "security team...
🔐 OWASP API Security — Why Every Developer Should Care (Java + AWS Context)
🌍 Summary APIs are everywhere — they power mobile apps, web services, and cloud-native...
OWASP Dependency Check
OWASP Dependency Check on Azure DevOps Atahan C. ・ Jan...
OWASP AppSec Days France 2025: Learning To Defend The Global Supply Chain Together
Paris is one of the most bustling metropolises on earth, with millions of locals going about their...
SnowFROC 2025: A Chilly Reminder That OWASP Matters and Exploring Secure Coding Practices with AI Coding Bots
Denver, Colorado, is home to vast mountain views of the easternmost section of the Southern Rocky...
Simple Root Detection: Implementation and verification
Read on Medium
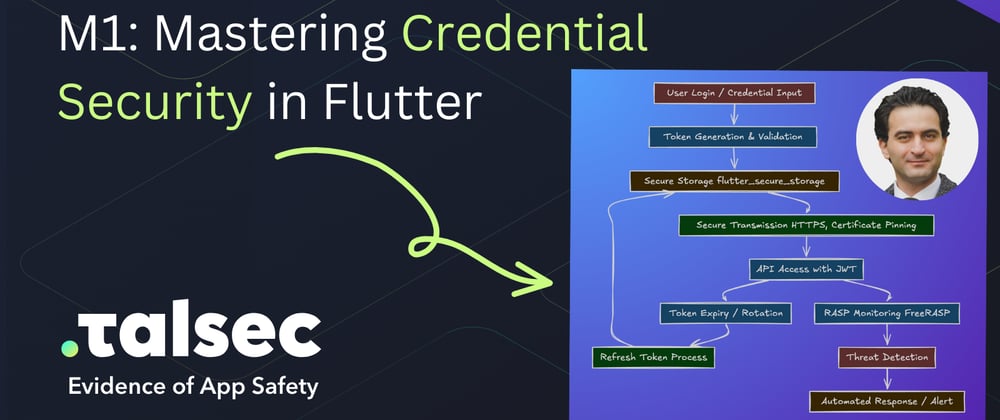
OWASP Top 10 For Flutter - M1: Mastering Credential Security
New series of articles covering OWASP Top 10 For Flutter by Majid Hajian Azure & AI advocate...
The logic of Value
Not all threats matters equally, and not all vulnerabilities hold the same relevance, unless analyzed...
OWASP Top 10–2021 | TryHackMe Write-up
Here is my article on the walkthrough of free room for TryHackMe: OWASP TOP 10 - 2021, which is the...
Understanding OWASP Top 10 for LLMs: A Layman’s Guide
In the world of AI, Large Language Models (LLMs) like GPT-4 and (o) are becoming increasingly...
OWASP Kubernetes Top 10 Explained: Know About Risks & Mitigation
What is Kubernetes? As open-source software, Kubernetes gives a platform to orchestrate...
Access Control Security: Learning from Major Data Breaches
Learn from Twitter, LastPass, and Uber data breaches with practical access control security examples....
Offensive security - Testing for Broken Access Control (OWASP)
Hands-on at tryhackme room #1.. I used dirb on CLI to brute-force hidden directories on a...
OWASP Dependency Check on Azure DevOps
I will start this blog post with what is OWASP? And I will continue with OWASP Top 10 known security...
Web App Security in 2025: Defending Against AI-Driven Attacks
How we stopped a zero-day LLM injection attack—and what’s coming next ...
Simple Root Detection: Implementation and verification
Read on Medium
OWASP Top Ten 2021 explained with simple Java examples and SAST insights
In this article, we talk about the OWASP Top Ten 2021 categories through the lens of PVS-Studio Java...
OWASP Top 10 Non-Human Identity Risks for 2025: What You Need to Know
The Open Worldwide Application Security Project, OWASP, has just released its Top 10 Non-Human...
OWASP Broken Access Control Vulnerabilities
When it comes to web application security, Broken Access Control stands out as one of the most...
Understanding Sequelize's 'escape' function and why ideally we should avoid using it manually
So a disclaimer. As a software engineer, I'm not a security expert. I rely heavily on those who know...