Articles by Tag #cloudwhistler
Browse our collection of articles on various topics related to IT technologies. Dive in and explore something new!
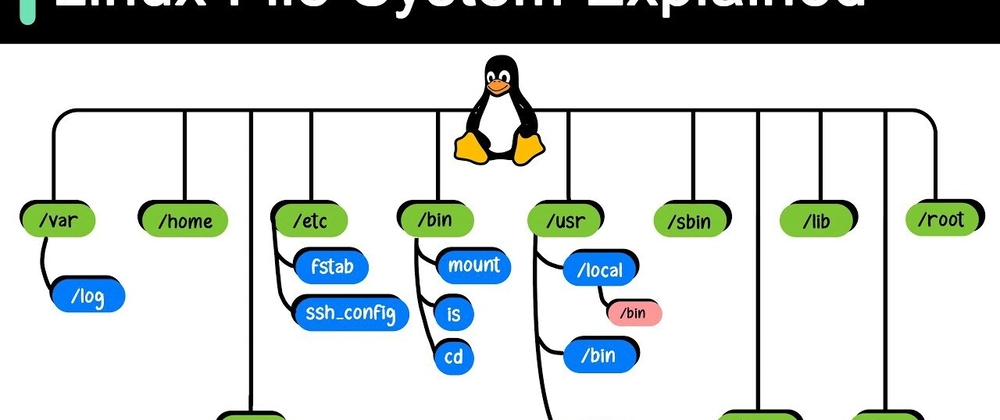
Inside the Linux Filesystem: Essential Knowledge for Cloud & DevOps Engineers
Table of Contents Introduction The Linux Filesystem Philosophy Bash: Your Command...
Linux Search Commands: Essential Tools for Incidence Response
Imagine this: a server in your production environment has been breached, and the security team...
Day 16/ 30 Days of Linux Mastery: Keyboard Shortcuts & Symbols
Table of Contents Introduction What Are Keyboard Shortcuts? Core Keyboard Shortcuts Core...
Day 11/ 30 Days of Linux Mastery: Setting Up a Local Repository Using RHEL 9 ISO
Table of Contents Introduction Why Repositories Matter Core dnf Repo Commands Real-World...
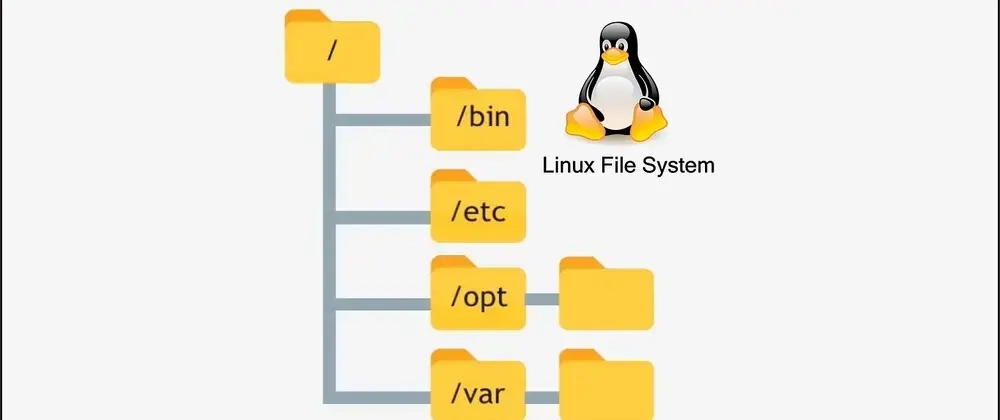
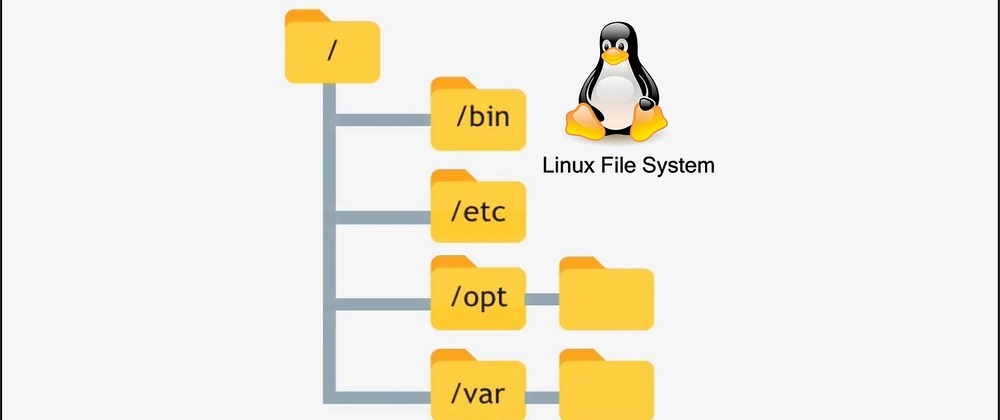
Understanding Linux File Hierarchy — A Beginner-Friendly Guide with Use Cases
If you're new to Linux, navigating its file hierarchy can feel like stepping into an entirely...
10 Daily Linux Questions and Answers Series (part 1)
In this brief article, I present 10 essential Linux questions along with their answers. This...
Move Over cat: Why Linux Users Should Embrace bat for a Better Terminal Experience
The Superior Alternative to Cat in Linux When working in Linux, the cat command is often the default...
Ansible + Red Hat: The Automation Alliance Powering Next-Gen Enterprise Infrastructure
There's a silent engine behind many of today's most reliable, scalable, and secure enterprise...
Day 20/ 30 Days of Linux Mastery: Recover/Rescue Root Password in RHEL9
Table of Contents Introduction Step-by-Step Guide on Recovering the Root...
Day 4 of 30 Days of Linux Mastery: Getting Comfortable with Vim
Table of Contents Introduction What is Vim? Understanding Vim Modes Core Vim Commands You...
The Cloud Security Blind Spots: What Most Cloud Engineers Don’t Know About Linux Security
In today's cloud first world, we're so caught up in configuring IAM policies, setting up security...
☠️ Never Run These! 10 Linux Commands That Can Destroy Your System
Have you ever been tempted to run a mysterious command you found online? STOP. Some Linux commands...
The Key to Control: Navigating Users, Groups, and Permissions
Table Of Content Introduction What Are Users, Groups, and Permissions? Getting to Know...
Simple Firewall with ufw or firewalld
Welcome to Day 16 of our Linux Security Basics series! After securing file permissions on topic 5,...
Why Linux Is Secure by Design (But Still Needs You)
Table Of Content Introduction What Makes Linux Secure by Design? Multi-User...
30 Days of Linux Mastery: From RHCSA to RHCE using Real-World Challenge Series
Table of Contents Introduction Day 1: Introduction to RHCSA, RHCE & Lab Setup What...
Linux File System
Index: Introduction / The Root Directory /root : The Root User’s Home /bin : Essential...
Hardening File Permissions: Practical Steps to Lock Down Data
Welcome to Day 15 of 30days linux challenge. We will be treating the 4th topic in our Linux Security...
How to Take Remote Backups Using rsync Over SSH (Day 12 of 30)
Table of Contents Introduction Why Organizations Still Use rsync Understanding rsync and...
🐧 Linux Won’t Bite: A Windows User’s First Taste of Penguin Power
The Confession: "I used to think Linux was for hackers and math geniuses. Then I tried it. Here's...
How Linux Can Change Your Approach towards Technology and Problem-Solving
You're capable of more than you realize. That nagging feeling that you're just scratching the surface...
Managing EC2 Instances with the AWS CLI
As a Cloud or DevOps engineer, proficiency and automation are key to managing a cloud infrastructure....
Day 29/ 30 Days of Linux Mastery: if Statements in Shell Scripting for Beginners
Table of Contents Introduction What is an if statement? Core if Statement...
Logs Don’t Lie: How to Turn Messy Files into Clear Wins for Your Team and Business
I remember the first time I was handed log files to separate into system and traffic logs. My eyes...
TERMINAL MASTERY: Master Linux File Commands in 10 Minutes Flat!
Give me 10 minutes, and I'll transform you from terminal newbie to command line wizard. Just pure...
Day 14/ 30 Days of Linux Mastery: Find Command
Table of Contents Introduction What is the find Command? Core find Commands Real-World...
What Keeps Red Hat So Damn Solid? Spoiler: It’s Not Luck, It’s Ruthless Kernel Engineering!
In the high-stakes enterprise environment where every second of downtime translates to lost revenue....
Top 25 Linux Commands You’ll Use Every Day (with examples)
Introduction As part of my RHCSA + RHCE Fast-Track Training with the Cloud Whistler...
Linux Essentials: How to Create, Read, and Delete Files & Directories Like a Pro
Whether you're just getting started with Linux or refreshing your command-line skills, mastering how...
Debug Smarter: How grep Helps Engineers Fix Issues Fast and Stand Out (Part 1)
In today's high pressure tech environments, the ability to quickly locate information isn't just...