Articles by Tag #dataprotection
Browse our collection of articles on various topics related to IT technologies. Dive in and explore something new!
Cloud Security Protecting Your Data in the Digital Sky
In today’s digital era, cloud technology has revolutionized how businesses and individuals store,...
The Privacy Paradox
Every time you unlock your phone with your face, ask Alexa about the weather, or receive a...
How to Break Free from Restricted Mailbox Limitations
In today’s world, we are constantly connected to each other through various means of communication....
The Impossible Promise
In December 2024, the European Data Protection Board gathered in Brussels to wrestle with a question...
Episode 3: Public RDS Detective — Finding Your Exposed Databases Before Attackers Do
Episode 3: Public RDS Detective — Finding Your Exposed Databases Before Attackers Do ...
Oracle Autonomous Database: Backup Management, Event Notifications, and Data Guard Protection
Oracle Autonomous Database provides comprehensive data protection through automated backup...
Compliance in Financial Web Apps: How to Build Secure, Trustworthy, and Regulation-Ready Applications
“We had the perfect fintech app—until compliance brought everything to a halt.” That was the...
Why Hackers Want Your Personal Data (And How They Use It)
Photo Credit: Unsplash / FLY:D Keypoints Your personal data has real monetary value...
That €20,000 Cookie: A Guide to GDPR Compliance for Website Owners
It started with a cookie. Literally. A small tech startup in Berlin thought they had it all...
Stop Storing Plain Text Passwords! Use Bcrypt for Security
When building an application that requires user authentication, one of the worst mistakes you can...
Mastering Your Digital Privacy: A Comprehensive Guide to Online Protection
Mastering Your Digital Privacy: A Comprehensive Guide to Online Protection ...
How AWS RDS Encryption at Rest Enhances Information Security
In today's data-driven world, securing sensitive information is crucial. AWS RDS Encryption at Rest 🔒...
How Small Businesses Can Implement Enterprise-Grade Security
In today’s digital-first world, data breaches and cyberattacks are no longer limited to large...
Your CMS Could Be Under Attack Right Now As I Write This — Here's How to Protect It
Picture waking up one day to discover your site — the cyber home you have spent months or years...
The Future of Cybersecurity Careers
Cybersecurity is one of the fastest-growing industries. AI and automation are reshaping job...
AI-Driven Cyber Attacks: The Next Evolution of Hacking
Artificial Intelligence is revolutionizing cybercrime. Hackers now use AI to automate phishing...
How Hackers Exploit IoT Devices
Billions of IoT devices expand the attack surface. Default passwords make them easy to...
The Rise of Deepfake Threats in Cybersecurity
Deepfake technology has become a cyber weapon. Attackers use fake videos to blackmail...
Cloud Security Challenges in 2025
Cloud adoption brings both opportunities and risks. Misconfigurations remain the leading cause of...
How to Ensure AWS S3 Bucket Security Best Practices
🚀 Secure your AWS S3 buckets like a pro! Follow these best practices to keep your data safe: ✅...
Industry-Specific Data Security: Protecting Sensitive Data Before It’s Too Late
Why every business must tailor its security strategy to its industry Imagine this: A mid-sized...
Zero Trust Security: Why It’s No Longer Optional
Traditional perimeter defenses are no longer effective. Zero Trust assumes no user or device is...
🔐 "My Password Wasn't Enough": Why You Need Multi-Factor Authentication Now More Than Ever
"But I had a strong password…" That was what my friend said, alarm in his tone, when he told me...
Why You Need an SSL Certificate: Benefits, Security, and SEO
Why You Need an SSL Certificate: Benefits, Security, and SEO Most websites collect...
ISMS Policies: What They Are and How They Can Prevent Cyber Attacks
In this digital era, computer security is a matter of great concern for organizations, regardless of...
Cybersecurity Essentials for the Modern Workplace
The modern workplace is more connected than ever—employees access data from anywhere, on any device....
The Future of Cybersecurity: Trends, Threats, and Innovations
Introduction Cybersecurity has never been more critical than it is today. As technology continues to...
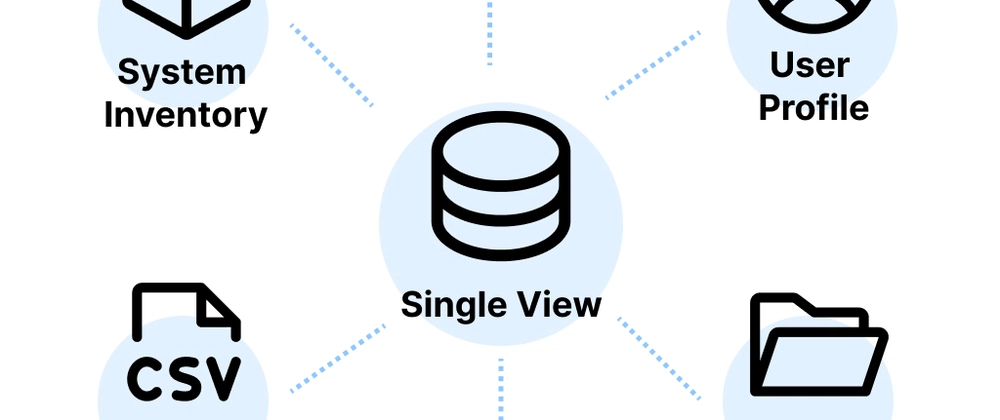
What Is a Single View?
According to Statista, 402.74 million terabytes of data are generated, imitated, and consumed daily....
Common GDPR Interview Questions
GDPR is a regulatory framework created to safeguard individuals' privacy and personal data in the...
“Privacy Risks of Smart Devices: What Your IoT Gadgets Reveal About You”
“Discover the hidden privacy risks of IoT devices. Learn how your smart gadgets track you and what...