Yurii Denchyk articles - 32 total
How to Detect Hooking (Frida) using Swift
On iOS, attackers equipped with Frida can hijack your app. DIY detection is fragile - serious apps...
How to Detect Hooking (Frida) using Kotlin
How to Detect Hooking (Frida) using Kotlin | by Talsec | Sep,...
How Secure Are Flutter Apps?
How Secure Are Flutter Apps? Security, Compliance, and...
How to prevent Time Spoofing with AppiCrypt.
Relying on device system time exposes app to - free trial abuse, license fraud, unfair gaming...
How to Detect Jailbreak using Swift.
How to Detect Jailbreak using Swift | by Talsec | Sep, 2025 |...
How to Detect Root using Kotlin
How to Detect Root using Kotlin. Need to secure your app...
Hardware-Backed Keystore
Ever wonder what really protects your phone's most sensitive data? It's not just software. Meet the...
A Guide to Countering GameGuardian with Talsec
GameGuardian's method of attack is deceptively simple yet profoundly damaging: it latches onto a live...
We tracked the App Integrity threat rate over 90 days, and the data is clear: the threat is constant and dynamic.
Talsec app integrity detection verifies your mobile App is the original, untampered version you...
Introducing Multi-Instancing Detection for freeRASP
another demanded feature for your mobile app security. docs.talsec.app
Introducing the Talsec Portal: A New Way to Monitor Your Mobile App Security — Try It Now!
docs.talsec.app
How to Achieve Root-Like Control Without Rooting: Shizuku's Perils & Talsec's Root Detection
How to Achieve Root-Like Control Without Rooting: Shizuku’s...
How to Achieve Root-Like Control Without Rooting: Shizuku's Perils & Talsec's Root Detection
How to Achieve Root-Like Control Without Rooting: Shizuku’s...
freeRASP for Unity
Good news for Unity Developers - now you can secure your game with freeRASP SDK from Talsec. Check...
ApkSignatureKiller: How It Works
ApkSignatureKiller: How It Works and How Talsec Protects Your...
Podcast: iOS Keychain vs Android Keystore
A post by Yurii Denchyk
Podcast: iOS Keychain vs Android Keystore
A post by Yurii Denchyk
AI-Powered Device Risk Summary | Android & iOS
watch on YouTube Article on Medium
OWASP Top 10 For Flutter – M6: Inadequate Privacy Controls in Flutter & Dart
OWASP Top 10 For Flutter — M6: Inadequate Privacy Controls in Flutter & Dart - this one offers...
How to Block Screenshots, Screen Recording, and Remote Access Tools in Android and iOS Apps
A post by Yurii Denchyk
Simple Root Detection: Implementation and verification
Read on Medium
Simple Root Detection: Implementation and verification
Read on Medium
OWASP Top 10 For Flutter — M5: Insecure Communication for Flutter and Dart
In this fifth instalment of our OWASP Top 10 series for Flutter developers, we shift focus to M5:...
OWASP Top 10 For Flutter – M4: Insufficient Input/Output Validation in Flutter
Welcome back to our deep dive into the OWASP Mobile Top 10, explicitly tailored for Flutter...
Transparent crash-tracking for production with PLCrashReporter
experts break down transparent crash-tracking solutions for production with PLCrashReporter, its...
M3: Insecure Authentication and Authorization in Flutter
is a part 3 in series of articles on OWASP Top 10 by expert Majid Hajian https://t.co/QCR9d8Lbgv
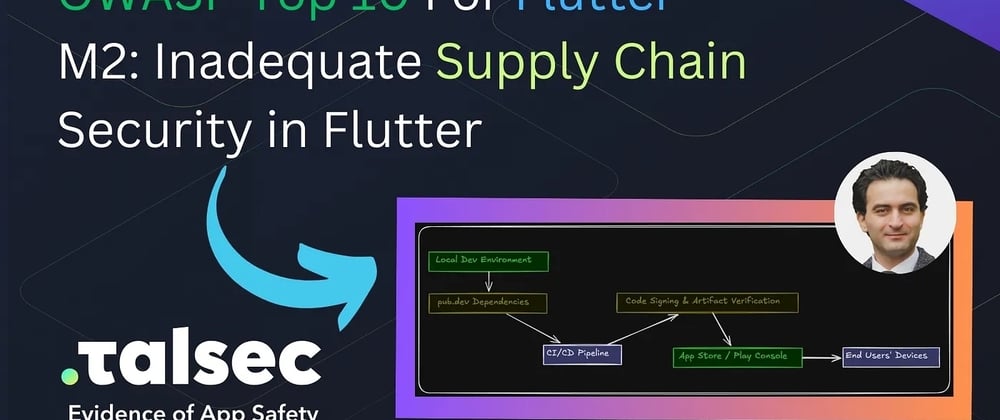
OWASP Top 10 For Flutter — M2: Inadequate Supply Chain Security in Flutter
Part two in series of articles covering OWASP Top 10 For...
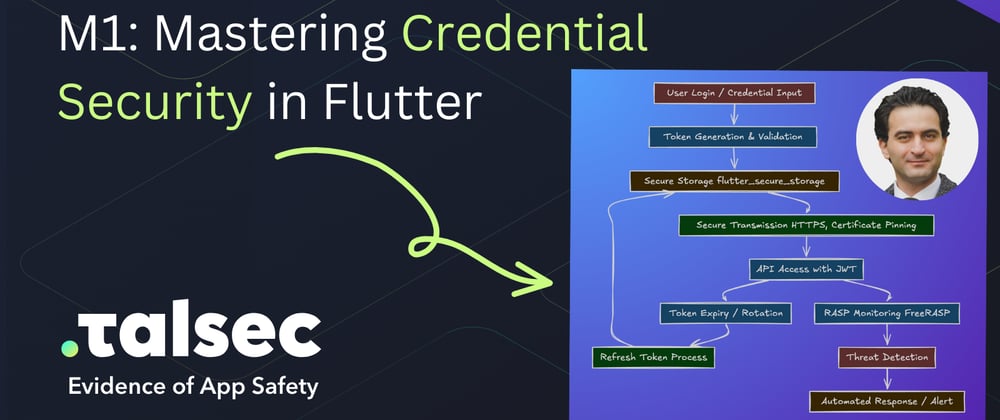
OWASP Top 10 For Flutter - M1: Mastering Credential Security
New series of articles covering OWASP Top 10 For Flutter by Majid Hajian Azure & AI advocate...
Hook, Hack, Defend: Frida’s Impact on Mobile Security & How to Fight Back
Talsec's engineer Akshit Singh explores how Frida works, the risks it poses to mobile apps, and why...
Emulators in Gaming: Threats and Detections
by Jaroslav Novotný, Senior Flutter Developer Android Emulators. What is an emulator, how can it...